Cybercriminals are already capitalizing on Twitter’s ongoing verification chaos by sending phishing emails designed to steal the passwords of unwitting users.
The phishing email campaign, seen by TechCrunch, attempts to lure Twitter users into posting their username and password on an attacker’s website disguised as a Twitter help form.
The email is sent from a Gmail account, links to a Google Doc with another link to a Google Site, which lets users host web content. This is likely to create several layers of obfuscation to make it more difficult for Google to detect abuse using its automatic scanning tools. But the page itself contains an embedded frame from another site, hosted on a Russian web host Beget, which asks for the user’s Twitter handle, password and phone number — enough to compromise accounts that don’t use stronger two-factor authentication.
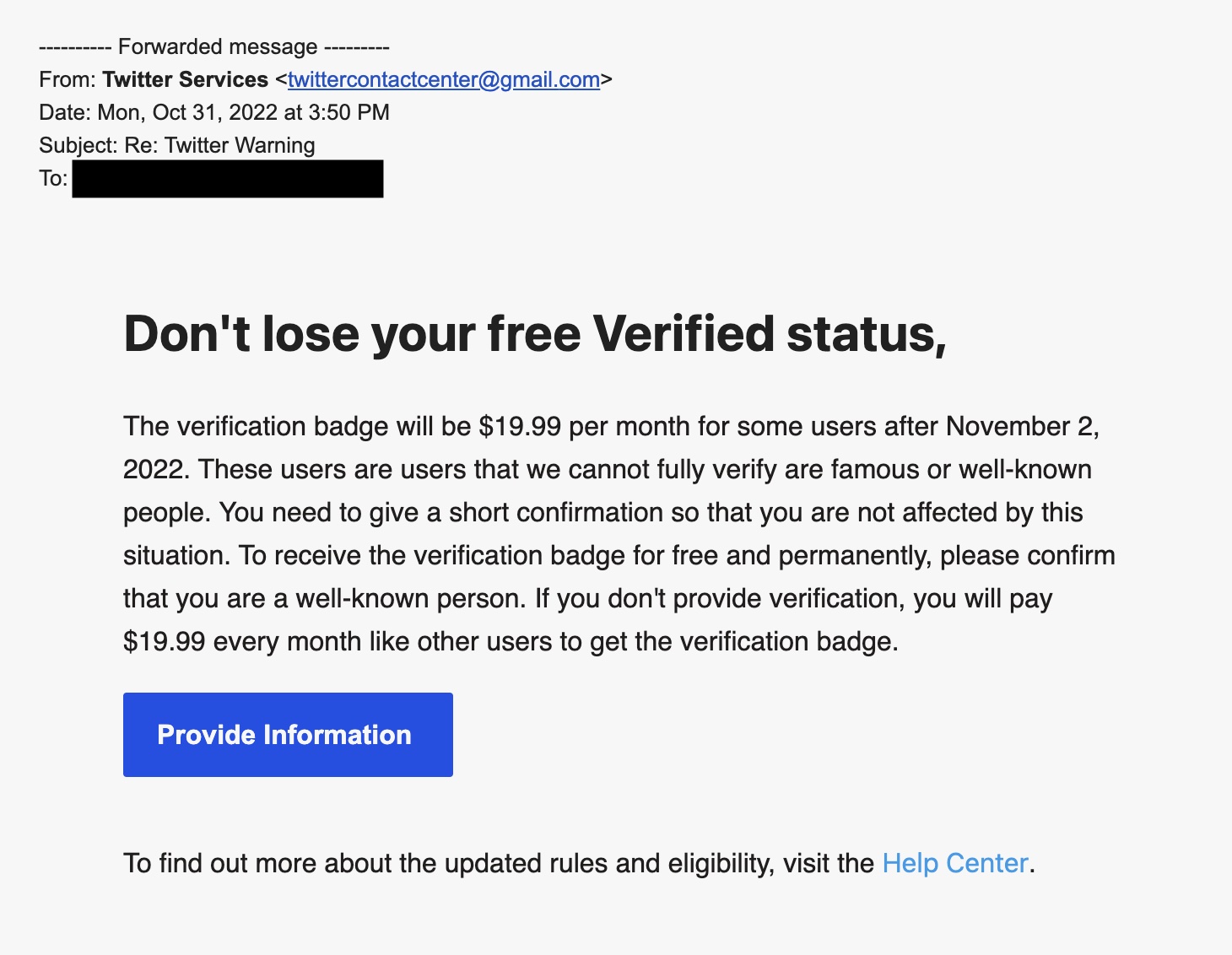
A screenshot of the phishing email designed to steal Twitter users’ credentials. Image Credits: TechCrunch.
The campaign appears crude in nature, likely because it was quickly put together to take advantage of the recent news that Twitter will soon charge users monthly for premium features, including verification, as well as the reported possibility of taking away verified badges of Twitter users who don’t pay.
As of the time of writing, Twitter has yet to make a public decision about the future of its verification program, which launched in 2009 to confirm the authenticity of certain Twitter accounts, such as public figures, celebrities and governments. But it clearly hasn’t stopped cybercriminals — even on the lower-skilled end — from taking advantage of the lack of clear information from Twitter since it went private this week following the close of Elon Musk’s $44 billion takeover.
TechCrunch has alerted Google and Beget to the phishing pages, but did not immediately hear back. A spokesperson for Twitter did not immediately respond to a request for comment.
Twitter’s verification chaos is now a security problem by Zack Whittaker originally published on TechCrunch
DUOS





