After talking about it for months, Twitter has finally released its first version of encrypted DMs — but there are a few limitations. Currently, this feature is only available to verified users (such as Blue subscribers) or accounts associated with verified organizations. Additionally, the encryption feature isn’t compatible with group messages and Twitter doesn’t offer protection against man-in-the-middle attacks.
Twitter said that while encryption works across platforms, the recipient has to follow the sender to enable it. Alternatively, encryption can be enabled if a user has chatted with the sender before, or accepted their DM request. If users are eligible for an encrypted conversation, the sender will get an option to turn on encryption through a toggle on the new chat screen.

Image Credits: Twitter
To turn on encryption for an existing conversation, you can tap on the information icon in the corner of the conversation screen and tap on the option that says “Start an encrypted message”. Encrypted conversations will look different from normal conversation as Twitter places a lock badge on the recipient’s profile picture. In the conversation itself, the company will show a “Messages are encrypted” banner at the top.
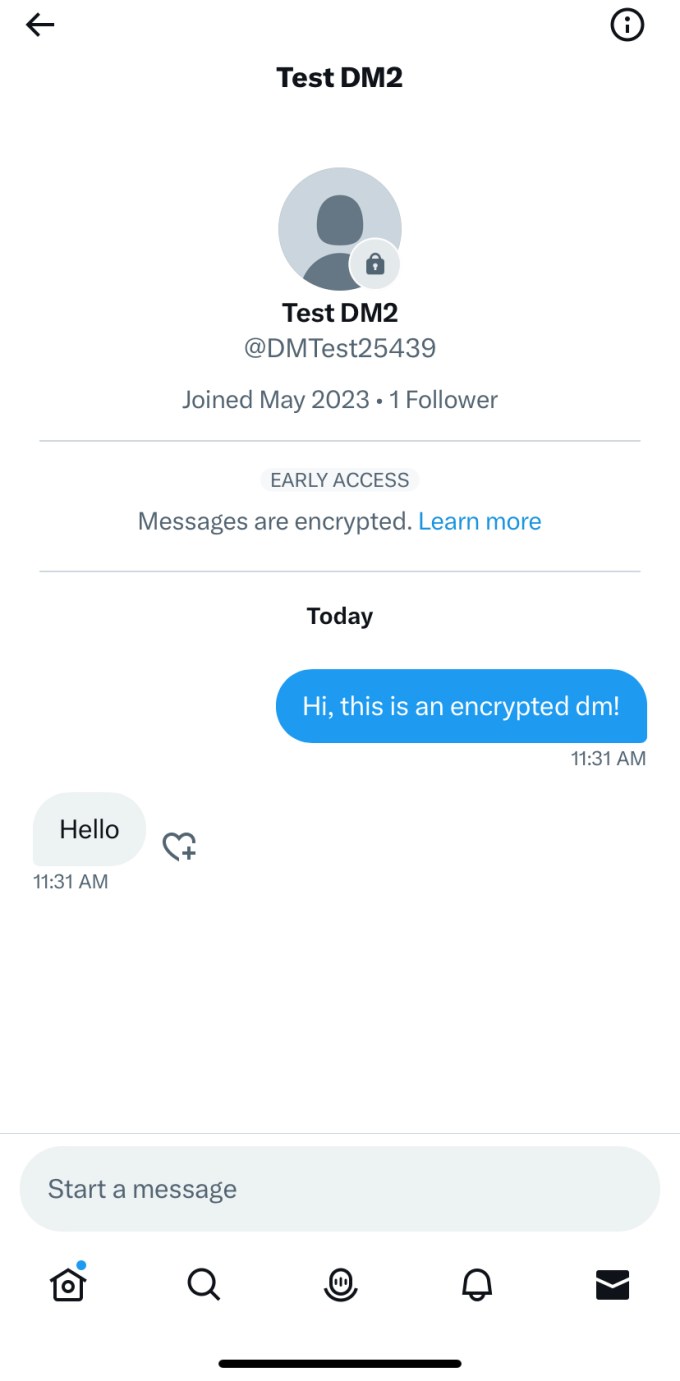
Image Credits: Twitter
The social network makes it clear in its blog post that there are several limitations to this implementation. On the conversational level, Twitter just supports encryption for one-to-one messages with text and links. Twitter said that media is currently not supported in encrypted conversations.
Additionally, people can’t use a new device to join an existing encrypted conversation. So you either have to use the same device with which you initiated an encrypted conversation or start a new conversation when you get a new device. Users can only use 10 devices in total to use the encryption feature, and there is no way to deregister a device to make room for a new one.
Notably, Twitter considers reinstalling the app as registering a new device. Twitter doesn’t offer a key backup option, which means that all your encrypted messages on that device will be wiped out if you log out of the account.
But the complex part is that Twitter doesn’t delete private keys from the device on logout — only messages. Users will be able to fetch existing conversations if they log in again from the same device. The company cautioned that people shouldn’t use the encryption feature on shared devices because of this limitation. This could change when Twitter starts offering a key backup option.
There are plenty of doubts about the feature’s security offering, too. It’s not clear what cryptographic standard Twitter is using for this feature. The company just said it is deploying “a combination of strong cryptographic schemes” in its blog post talking about the encryption feature.
Twitter said that its encryption feature also doesn’t offer forward secrecy protection, so an attacker can access all of a user’s past conversations if they get access to a compromised device. The company said it decided not to implement this feature to let users access their unencrypted DMs on any device.
At the moment, Twitter doesn’t offer signature checks or message verification features. So devices themselves can’t check the authenticity of the message and people can’t use methods like comparing number strings to verify encryption protection.
This makes the system vulnerable to man-in-the-middle attacks. That means an attacker can read your messages if the security is compromised. Twitter also hinted that it could give this conversation up to authorities as part of a legal process due to the current design flaws.
“As a result, if someone — for example, a malicious insider, or Twitter itself as a result of a compulsory legal process — were to compromise an encrypted conversation, neither the sender nor receiver would know,” the company said. Twitter wants to add signature checks and safety numbers so that these attacks or requests are no longer possible.
After taking over the company, Elon Musk has expressed his desire to “superset Signal” with Twitter DMs. However, with the current set of limitations, it doesn’t offer the same level of protection that Signal or other apps offer. Both Signal and WhatsApp offer end-to-end encryption for all kinds of conversations. Additionally, Signal doesn’t log any metadata about contacts or messages.
“As Elon Musk said, when it comes to Direct Messages, the standard should be, if someone puts a gun to our heads, we still can’t access your messages. We’re not quite there yet, but we’re working on it,” the company said.
Twitter launches encrypted DMs for verified users with security drawbacks by Ivan Mehta originally published on TechCrunch
DUOS





